Humans find what automation can’t.
Put the world’s largest community of ethical hackers to work for you.
What is human-powered security?
Human-powered security taps into the skills and creativity of ethical hackers to identify critical vulnerabilities before cybercriminals do. These vetted security researchers simulate real-world attacks to uncover your critical risks and help you fix them fast.
Who are these ethical hackers? They range from full-time security researchers to seasoned security engineers to teen prodigies, university professors, medical doctors, and experienced penetration testers.
HackerOne matches you with thoroughly vetted, top-notch security talent from our global community of 2M+ hackers. 91% of HackerOne customers say hackers provide more impactful and valuable vulnerability reports than AI or scanning solutions.
Learn more about working with ethical hackers →

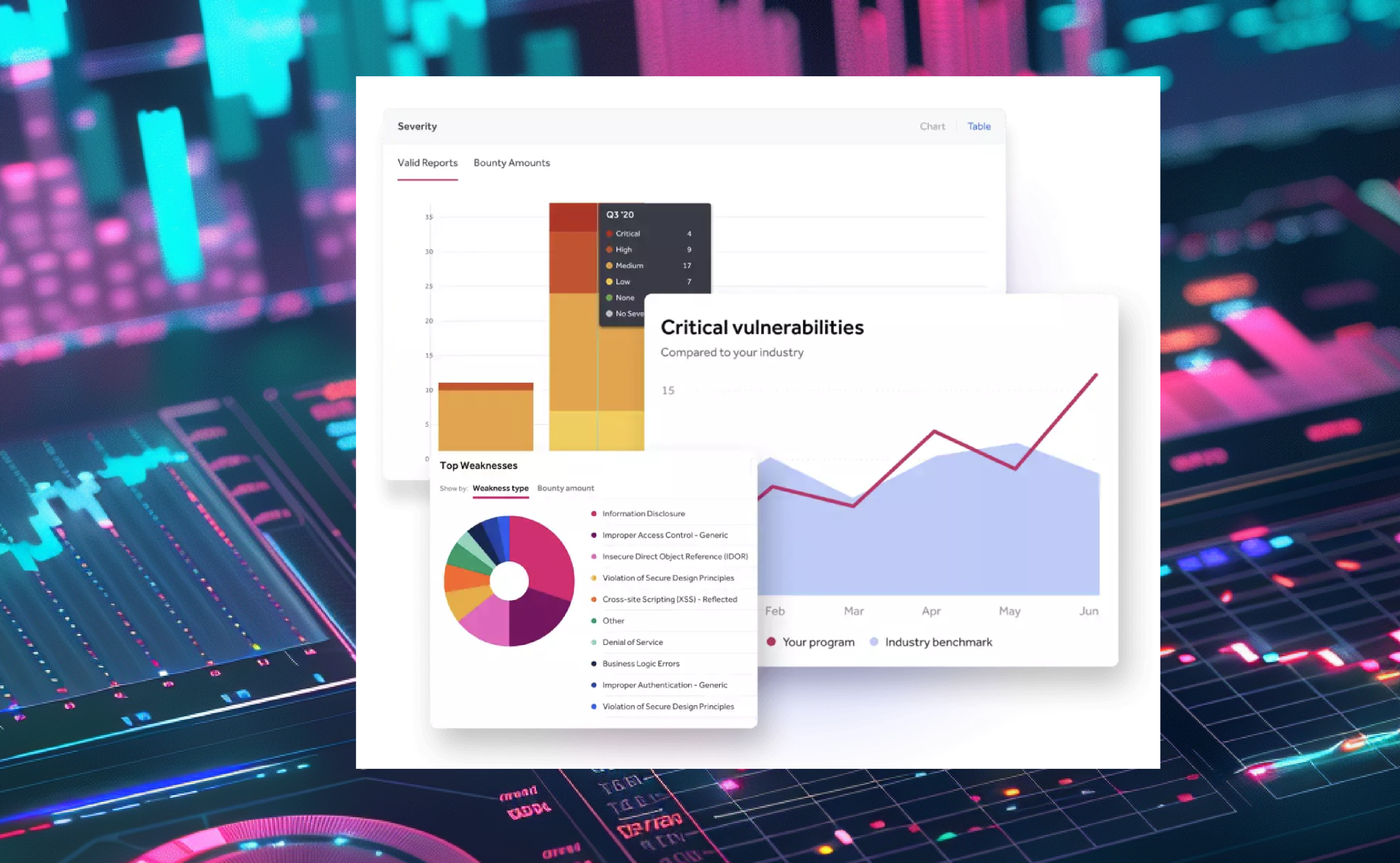
Seamlessly manage pentests, bug bounties, vulnerability disclosure, and code review in one place—fulfilling your evolving needs for continuous, preemptive security testing.

We start by gaining a deep understanding of your security goals and challenges, then work with you to design a program that meets your needs. Our ultimate aim is to help you maximize your programs’ ROI and measurably reduce your risk.

We go beyond simple SLA-based intake—validating each vulnerability's legitimacy, severity, and impact. The result: a customer satisfaction score of 4.71 out of 5.

Track key metrics like response times, report submissions, rewards paid, and remediation statuses in real time. Leverage our vast dataset and proprietary AI to benchmark your program against industry peers and forecast trends.
How can human-powered security help you?
Growing attack surfaces. Rapid AI proliferation. Faster SDLCs than ever before. The devastating cost of a breach. The security skills shortage.
Traditional security tools and methods are no longer sufficient to keep you ahead of cybercrime. But a vast global community of ethical hackers can work 24x7 to uncover hidden weaknesses in your systems before bad actors do.
70%
of HackerOne customers say hacker efforts have helped them avoid a significant security incident. 1
$4.45M vs. $3.7k
The average cost of a data breach exceeds $4.45 million. 2 The average bug bounty paid to a hacker for a high- or critical-severity vulnerability is just $3,700. Human–powered security can pay for itself with just a single vulnerability report.
62%
of hackers in HackerOne's annual survey plan to specialize in the OWASP Top 10 for LLM Applications, using their unique perspectives to uncover weaknesses that traditional security measures might miss. Human-powered AI red teaming can keep you ahead of the curve in identifying and mitigating AI-related vulnerabilities.





“Don’t underestimate the creativity of hackers. Everyone comes at it with a different lens, different expertise, and different experience. We don’t want to leverage the community to approach a problem in the same way we would approach a problem. Our software becomes more secure when we open it up to diverse mindsets.”

“In the security industry we have a ton of blind spots…and it’s the purpose of this insanely useful [hacker] community to tell us about the blind spots.”

"It’s a substantial investment, but the returns are worth it. We harness world-class talent to find real-world solutions before it’s a real-world problem."

“The main value that I communicate to the board is that HackerOne helps us find out what we don't know and helps us see around corners. That resonates very well with the executive team at Grammarly. It’s not just that we fixed 15 new vulnerabilities this month; it’s typically a bigger conversation where I share anecdotes about how reports have led to more insights and investments."
How it works
Schedule a Personalized Demo
See how you can detect and resolve vulnerabilities before they are exploited.







